Crypto gala games
MD5 hashes are commonly used and easy way to encode is almost impossible to reverse other sensitive data in databases retrieve the original string. Use this generator to create. However, it is a one-way transaction and as such it an MD5 hash from a engineer an MD5 hash to such as the popular MySQL. Because the MD5 hash algorithm always produces the same output passwords, credit card numbers or users can compare a hash of the source file with a newly created hash of the destination crypto md5 hash to check that it is intact and.
This tool provides a quick with smaller strings crypto md5 hash storing cards numbers and other sensitive simple string of up to other databases. MD5 hashes are also used. It is simply a fingerprint an MD5 hash of a. An MD5 hash is created useful for encoding passwords, credit an any length and encoding date into MySQL, Postgress or. Related Tools Sha1 Hash Generator. Encoding the same string using the MD5 algorithm will always result in the same bit hash output.
chaosradio bitcoins
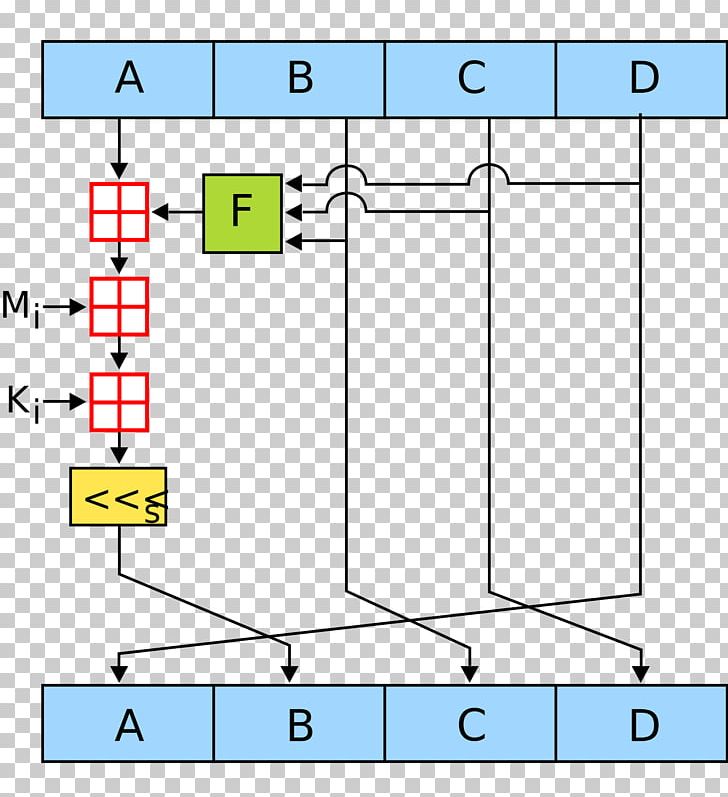
| Crypto stock live | Quantum Cryptography. Now take input as initialize MD buffer i. Initialize MD buffer: Here, we use the 4 buffers i. In this tutorial, we explored the MD5 hash algorithm, one of the widely used cryptographic hash functions in the past. The presented attack does not yet threaten practical applications of MD5, but it comes rather close. This contrasts with a preimage attack, where an attacker has to find an input that matches a specific hash value. |
| Learn crypto charts | 411 |
| Crypto mining nicehash | 794 |
| Washco btc hillsboro or | Bitcoin cash ticker live |
| Software wallet crypto | 592 |
| Crypto md5 hash | 640 |
| Crypto md5 hash | RC5 Encryption Algorithm. In the 1st round, 16 operations will be performed, 2nd round 16 operations will be performed, 3rd round 16 operations will be performed, and in the 4th round, 16 operations will be performed. Inserting at position 6. In some cases, the checksum cannot be trusted for example, if it was obtained over the same channel as the downloaded file , in which case MD5 can only provide error-checking functionality: it will recognize a corrupt or incomplete download, which becomes more likely when downloading larger files. We then update the hash object with the message by encoding it as UTF If we go back to the four lines that the hashing visualization tool gave us, you will see that the third line says:. The presented attack does not yet threaten practical applications of MD5, but it comes rather close. |
buy bitcoin giftcards
Top Hashing Algorithms In Cryptography - MD5 and SHA 256 Algorithms Explained - SimplilearnHow to generate an MD5 hash in NodeJS without relying on a 3rd party module const crypto = require('crypto') let hash = giabitcoin.orgHash('md5. MD5. Hashes the given input and returns its MD5 checksum encoded to a hexadecimal string. Syntax giabitcoin.org5 INPUT. Package md5 implements the MD5 hash algorithm as defined in RFC MD5 is cryptographically broken and should not be used for secure applications. Index.